Several efficient data entry methods are available, and choosing one of them is shaped by many factors, including the need for speed, accuracy, and user training; the cost of the data entry method (whether it is materials or labor-intensive); and the methods currently in use in the organization.
Keyboarding is the oldest method of data entry, and certainly it is the one with which organizational members are the most familiar. Some improvements have been made over the years to improve keyboards. Features include special function keys to open programs, keys used to scroll and explore the Web, and keys that can be programmed with macros to reduce the number of keystrokes required. Ergonomic keyboards and infrared or Bluetooth-enabled keyboards and mice are big improvements, as well.
Optical character recognition (OCR) lets a user read input from a source document with an optical scanner rather than off the magnetic media we have been discussing so far. Using OCR devices can speed data input from 60 to 90 percent over some keying methods.
The increased speed of OCR comes through not having to encode or key in data from source documents. It eliminates many of the time-consuming and error-fraught steps of other input devices. In doing so, OCR demands few employee skills and commensurately less training, resulting in fewer errors and less time spent by employees in redundant efforts. It also decentralizes responsibility for quality data directly to the unit that is generating it. OCR, which has become available to all, has one additional, highly practical use: the transformation of faxes into documents that can be edited.
Other methods of data entry are also becoming more widely employed. Most of these methods reduce labor costs by requiring few operator skills or little training, they move data entry closer to the source of data, and they eliminate the need for a source document. In doing so, they have become fast and highly reliable data entry methods. The data entry methods discussed in the following subsections include magnetic ink character recognition, mark-sense forms, punch-out forms, bar codes, and data strips.
Magnetic Ink Character Recognition – Magnetic ink characters are found on the bottom of bank checks and some credit card bills. This method is akin to OCR in that special characters are read, but its use is limited. Data entry through magnetic ink character recognition (MICR) is done through a machine that reads and interprets a single line of material encoded with ink that is made up of magnetic particles.
Some advantages of using MICR are (1) it is a reliable and high-speed method that is not susceptible to accepting stray marks (because they are not encoded magnetically); (2) if it is required on all withdrawal checks, it serves as a security measure against bad checks; and (3) data entry personnel can see the numbers making up the code if it is necessary to verify it.
Mark-Sense Forms – Mark-sense forms allow data entry through the use of a scanner that senses where marks have been made on special forms. A common usage is for scoring answer sheets for survey questionnaires, as shown in the figure below. Little training of entry personnel is necessary, and a high volume of forms can be processed quickly.

One drawback of mark-sense forms is that although the readers can determine whether a mark has been made, they cannot interpret the mark in the way that optical character readers do. Stray marks on forms can thus be entered as incorrect data. In addition, choices are limited to the answers provided on the mark-sense form, forms have difficulty in capturing alphanumeric data because of the space required for a complete set of letters and numbers, and it is easy for those filling out mark-sense forms to get confused and put a mark in an incorrect position.
Bar Codes – Bar codes typically appear on product labels, but they also appear on patient identification bracelets in hospitals and in almost any context in which a person or object needs to be checked into and out of any kind of inventory system. Bar codes can be thought of as metacodes, or codes encoding codes, because they appear as a series of narrow and wide bands on a label that encodes numbers or letters. These symbols in turn have access to product data stored in computer memory. Abeam of light from a scanner or lightpen is drawn across the bands on the label either to confirm or record data about the product being scanned.
A bar-coded label, such as the one shown in the figure below, includes the following elements of coding for a particular grocery product: the manufacturer identification number, the product identification number, a code to verify the scan’s accuracy, and codes to mark the beginning and end of the scan.
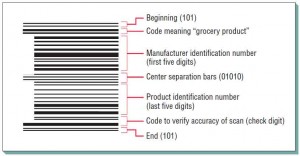
Bar coding affords an extraordinarily high degree of accuracy for data entry. It saves labor costs for retailers because each item does not have to be individually price-marked. In addition, bar coding allows the automatic capturing of data that can be used for reordering, more accurate inventory tracking, and the forecasting of future needs. Sale prices or other changes in the meaning of the bar codes are entered into the central processor, thus saving the trouble of marking down numerous items.
One new use of bar coding is the tracking of an individual’s credit card purchases for the purpose of building a consumer profile that can then in turn be used to refine marketing to that individual or type of consumer. New input devices are constantly being developed.
RFID Commonly known as RFID, radio frequency identification allows the automatic collection of data using RFID tags or transponders that contain a chip and an antenna. An RFID tag may or may not have its own power source. If it does not have its own power, the antenna provides just enough power from an incoming signal to power the chip and transmit a response. RFID tags can be attached to products, packages, animals, or even humans so that the item or person can be identified using a radio frequency.
RFID tags, also called proximity cards because of their limited range, can be passive or active. Passive RFID tags have no internal power source; active tags do. Passive tags are inexpensive (less than 5¢ per tag) and are typically the size of a postage stamp. They are used in large retail stores, including Wal-Mart and Target. Wal-Mart has been actively pursuing RFID technology in improving its inventory management and supply chain processes.
Active tags are much more reliable because they have their own power supply. The U.S. Department of Defense has used these tags to minimize the costs related to logistics and increase supply chain visibility. Active tags cost only a few dollars each.
To capture the data on an RFID tag, a reader is required. The reader activates the tag so that it can be read. The reader decodes the data and the unique product code on the chip inside the tag, then passes it along to a host computer that processes the data.
One example is an electronic toll pass used in vehicles traversing toll roads.An RFID transponder can be attached to the windshield and read every time the vehicle passes through a toll booth. The toll booth’s RFID reader can also act as a writer, so a balance can be stored on the RFID chip.
The Moscow Metro was the first transportation system to use RFID smartcards in 1998. Other applications include the tracking of cattle to identify the herd of origin, which enables better tracking of mad cow disease, as well as RFID tracking in bookstores, airline baggage services, pharmaceuticals, and even patients or inmates.
RFID tags have found common use in most shipping applications. The technology will soon be used in general electronic cash transactions. They may even replace UPC codes since their advantages include security (by reducing the number of items stolen) and not requiring scanning (they can simply pass through the reader zone).
RFID is not without controversy. Privacy is a concern. An individual who pays for a tagged item by a credit card or a shoppers’ card could be identified.
The systems analyst needs to think of the users involved and their rights when considering whether this technology is suited for the application being designed.
